The need for joint cybersecurity operations across EU Members States and the JCOP project
Author: Sphynx Analytics Ltd (SANL) Since digital technologies become more pervasive in everyday lives and economies, cybersecurity incidents are getting frequent and diversified. Data breaches exposed 4.1 billion records in the first half of 20191, while the recently-released ENISA Threat Landscape for 2020 states that “during the next decade, cybersecurity risks will become harder to assess and interpret due to the growing complexity of the threat landscape, adversarial ecosystem and expansion of the attack surface”2, reporting an increase in sophisticated and targeted ransomware exploits in the public sector, health care organisations and other industries, as well as the increased prevalence of hybrid threats, combing both the cyber and physical domains. The COVID-19 pandemic has also exacerbated the risk exposure, being identified by ENISA as a “prolific period for malicious actors conducting attacks targeting sensitive areas”3.
In this context, threats in cyberspace endanger not only our democracies and freedoms but also the European long-term objectives, such as the Digital Single Market that aims to enhance Europe's position as a world leader in the digital economy. Both civilian and military European environments should be able to protect against cyber threats. Thanks to the NIS Directive (2016/1148), Member States are now forced to have a minimum baseline set of capabilities while providing cross-border coordination and cooperation. In fact, in the cybersecurity domain, 69% of companies confirm that compliance mandates driving spending4, while companies reportedly spent $9 billion on preparing for the GDPR5.
Nevertheless, regulatory drivers are not enough. Dealing with systemic and complex risks is highlighted as the top cybersecurity challenge by ENISA, since the increased motivation (often combining financial, nation state interests, nationalistic and political motives) and sophistication of threat actors (often state-sponsored) carrying out growing targeted and persistent attacks on high-value data, combined by the ever-increasing interconnectedness of various systems and networks, make “cyber risks harder to assess and mitigate”. In this regard, ENISA's policy conclusions and recommendations highlight the importance of using Cyber Threat Intelligence (CTI) as the main tool for cybersecurity preparedness and driving strategic and political decisions that will effectively tackle threats that threaten the well-being of the European Union. It is also emphasized that cooperation and coordination of EU-wide CTI activities are essential for informing and driving emergency decisions needed in crisis management6. Moreover, having access to a cyber-range and other structured training means are highlighted as essential enablers for building the skills of security teams by simulating attacks and testing multiple defence strategies.
The above are very much aligned with the recommendations provided in the European Commission Recommendation on Coordinated Response to Large Scale Cybersecurity Incidents and Crises7 (referred to henceforth as “Cyber Blueprint”), which aims to provide a structured approach towards shared situational awareness, preparedness and coordinated incident response that also considers and involves all key EU actors involved in response to cybersecurity crises (e.g., ENISA, CSIRTs network, CERT-EU, Europol). Of particular interest in this regard is the newly launched Cyber Crisis Liaison Organisation Network8 (CyCLONe) that aims to contribute to the Blueprint's implementation and complements the existing EU cybersecurity structures by linking the cooperation at technical, operational and political/strategic levels.
Motivated by the above, the European Commission, under the Connecting Europe Facility 2014-2020 programme, launched the JCOP project (Agreement No.: INEA/CEF/ICT/A2020/2373266) in August 2021, aiming to design, develop and deliver a Joint Cybersecurity Operations Platform tailored to the needs of EU Member State authorities entrusted with cybersecurity, encompassing a toolbox and methods facilitating shared situational awareness, preparedness and coordinated incident response in alignment with the NIS Directive-established EU cybersecurity structures and mechanisms.
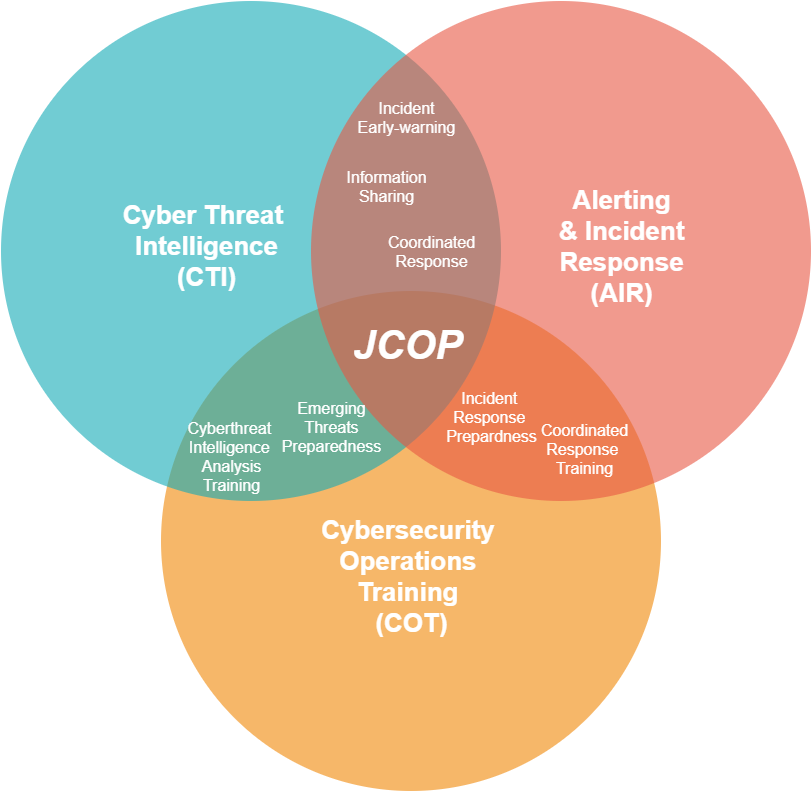
To achieve its objective and provide a holistic Cybersecurity Operations solution, the platform will include:
- Cyber Threat Intelligence (the “CTI” pillar);
- Alerting & Incident Response (the “AIR” pillar), and;
- Cybersecurity Operations Training capabilities (the “COT” pillar).
Figure 1 visualises the above three pillars of the JCOP concept, as well as the interplay between them. The latter, realised through tight interconnection & continuous feedback between each pillars' capabilities, will allow operators to fully exploit & maximise the efficacy of each capability, and eventually maximise the overall usability & impact of JCOP.
The above will be deployed and validated through the creation of a model Southeast Europe Coordinated Response Cluster encompassing the national authorities of Greece (Hellenic Ministry of Digital Governance - National Cyber Security Authority - NCSA) and Cyprus (Cypriot Digital Security Authority - DSA). This will not only demonstrate in practice the capacity- and coordination- building impact of JCOP at the national (between national JCOP instances) and the EU level (between JCOP instances and EU cybersecurity bodies, such as the CSIRTs network, CERT-EU, and ENISA), but will also help establish JCOP as a prototypical implementation of the Cyber Blueprint and a reference that can be applied to additional Member States. The inclusion of an additional national authority in the consortium (Norwegian National Security Authority - NSM) will allow the accurate assessment of said applicability in other Member States.
Throughout the action, JCOP will be aligned with pertinent EU platforms and initiatives, such as the MeliCERTes9 cybersecurity platform, the EU ISACs project for information sharing between CIs10, and the four pilots of the EU Cybersecurity Competence Network11. Further, in order to ensure that JCOP's activities will be in line with the EU cybersecurity strategy as a whole, the action will closely follow and adopt, tools and blueprints delivered by NIS Cooperation Group12, ENISA13, EU ISACs14, ECSO15, exploiting the outcomes of JRC16 (such as the cyberthreat taxonomy17).
Watch this space for more interesting blog posts in the coming months, analysing various aspects of JCOP's approach, and do not forget to monitor the project website and our LinkedIn page for updates on the latest project activities.
Resources- https://pages.riskbasedsecurity.com/2019-midyear-data-breach-quickview-report
- ENISA Threat Landscape 2020 - Emerging trends
- ENISA Threat Landscape 2020 - Main Incidents
- https://www.csoonline.com/article/3153707/top-cybersecurity-facts-figures-and-statistics.html
- https://www.forbes.com/sites/oliversmith/2018/05/02/the-gdpr-racket-whos-making-money-from-this-9bn-business-shakedown/#2df4db1134a2
- ENISA Threat Landscape 2020 - The year in review
- Commission Recommendation (EU) 2017/1584 of 13 September 2017 on coordinated response to large-scale cybersecurity incidents and crises
- https://www.enisa.europa.eu/news/enisa-news/blue-olex-2020-the-european-union-member-states-launch-the-cyber-crisis-liaison-organisation-network-cyclone
- https://ec.europa.eu/inea/en/connecting-europe-facility/cef-telecom/2017-es-ia-0055
- https://www.isacs.eu/
- https://cybercompetencenetwork.eu/
- https://ec.europa.eu/digital-single-market/en/nis-cooperation-group
- https://www.enisa.europa.eu/
- https://www.isacs.eu/
- https://ecs-org.eu/
- https://ec.europa.eu/info/departments/joint-research-centre_en
- https://ec.europa.eu/jrc/en/science-update/european-cybersecurity-taxonomy
