OASIS CACAO v2.0 standard is released
Author: Bret Jordan, Vasileios Mavroeidis (UiO), Luca Morgese, and Allan Thomson 
Introduction
Organizational cyber security has never been more under attack than in today's world. With the introduction of the OASIS Collaborative Automated Course of Actions Operations (CACAO) Version 2.0 standard, security organizations have a new and formidable toolkit in their ability to orchestrate and collaborate using fully automatable security playbooks to respond to today's cyber threats.
Read on to learn more about how CACAO can help defend your organization better.
The New Standard for Security Playbooks
CACAO is a standardized framework for orchestrating and automating course-of-action playbooks in cybersecurity. It streamlines the creation, execution, and sharing of playbooks, making it easier for security teams to respond to incidents, mitigate threats, and protect their networks. CACAO offers a modular and extensible approach to playbook development, ensuring that it can adapt to the diverse needs of different organizations.
CACAO focuses on empowering IT/Security organizations to design and orchestrate security activities. These range from traditional activities like intrusion detection; through security event triage, to determining relevant steps to counter a threat; and enforce mitigation and incident response procedures.
Moreover, it enables more advanced techniques that use playbooks across various use cases that organizations may employ or want to address, such as performing attack emulations as part of red team activities, utilizing threat deception techniques to engage with active threats against the organization, or even ensuring policy and regulatory compliance.
The following section highlights some of the key aspects of how CACAO Playbooks are designed.
Key Technology of CACAO
Figure 1: Key components of CACAO.
Organizing and Searching Playbooks: Metadata
Metadata is a crucial and powerful component of CACAO, allowing for the efficient categorization and searchability of playbooks. It includes information such as the operational roles a playbook performs, descriptions of its activities, and the complexity of workflow steps encapsulated. For example, a playbook may contain workflow steps that are simple sequencing or they may contain control flows that require the orchestration system to handle the typical logic that programs require. This metadata helps organizations find relevant playbooks quickly and accordingly tailor them to their specific requirements.
Defining the process, logic and knowledge within a playbook: Workflow Steps
CACAO playbooks are structured as workflows, composed of a dictionary of action steps to be performed sequentially or in parallel while also staying flexible, allowing branching with other CACAO playbooks (modular approach), and incorporating different types of conditional logic (e.g., if, while, switch) to support even the most advanced and complex scenarios and requirements.
Connecting the playbook steps to systems, people and their targets: Agents and Targets
In CACAO, the agent is the entity responsible for executing actions, while the target is the recipient of those actions. Agents execute action steps containing commands against targets. The design emphasizes modularity and reusability, allowing organizations to define agents and targets once, reference them in multiple playbooks, or reuse them within a playbook. This approach provides flexibility on how action steps and their underlying commands will be executed by, or against, for example, an individual, group, organization, devices and equipment, or in a hybrid manner.
Additional Key Features of CACAO

Figure 2: 1. Modularity & Extensibility.
1. Recognizing that cybersecurity organizations and their technologies can span a large ecosystem that is constantly evolving, CACAO was designed to be both modular and extensible.
Organizations can be responsible for specific areas of technology and their respective playbooks. Those playbooks can be combined with other organization's playbooks for specific threats or general process implementation that larger organizations typically follow when responding to incidents (also known as standard operating procedures - SOPs). In many respects how the IT/Security organization is defined and operating is set; however, CACAO playbooks can be easily mapped to that organizational fit, without requiring changes to the organization or how they perform their automation. With CACAO, organizations now have standardized and fully interoperable playbooks that can provide significant improvements to their operational processes within the organization and externally if the team is collaborating with other organizations.
CACAO already includes a comprehensive set of integrations for a large variety of commands and toolsets*. However, organizations can also adapt CACAO to incorporate new tools, proprietary systems, or evolving industry standards. We defined an extension mechanism that is now the basis for STIX and CACAO Extensions that can be applied at the playbook, step, or command level, providing flexibility for organizations to customize their orchestration.
* See CACAO Specification Section 5 for details.

Figure 3: 2. Ensuring Playbook Integrity.
2. Integrity and trust are essential in the world of cybersecurity. CACAO addresses this need by incorporating digital signatures into playbooks to support the ability for them to be signed and countersigned. CACAO's signature mechanism (JSON signature scheme), has been submitted to the UN's ITU-T, which was standardized as X.590. It is now being used in CACAO, assuring authenticity and ensuring integrity across playbooks and helping organizations validate their sources and track changes to playbooks over time.
Figure 4: 3. Integrating Cyber Threat Intelligence (CTI) with Orchestration.
3. CACAO connects with the Structured Threat Information eXpression (STIX) Version 2.1 standard, ensuring interoperability and information sharing between cyber threat intelligence and incident response. CACAO uses the same identifiers, versioning mechanism, and core metadata as STIX, enabling organization investments to support both standards easily. This integration allows organizations to leverage their cyber threat intelligence knowledge and apply it directly to their playbooks. Similarly, the synergistic utilization of these two standards can allow CTI to trigger or recommend the execution of specific CACAO playbooks.
Designing CACAO Playbooks - Key Elements to Consider
As highlighted above, there are three key aspects to designing a CACAO Playbook that an organization must consider.
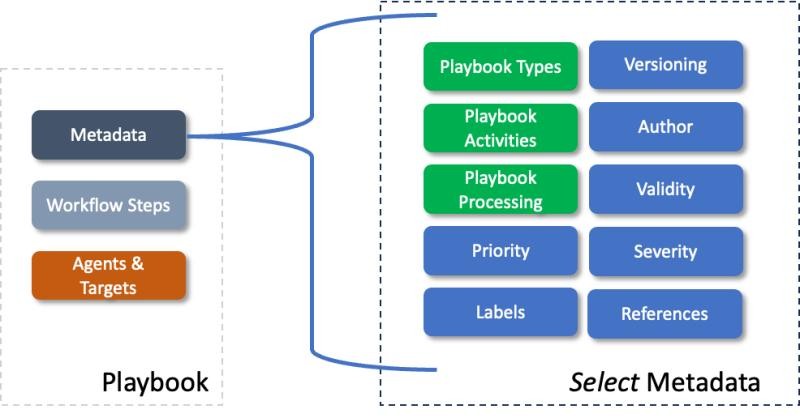
Figure 5: CACAO Playbook Metadata.
Metadata enables organizations to assess and evaluate the contents of a playbook and what its operational impact might be. The key parts and some of the properties to consider are:
- Playbook Type: This property defines the key purpose of the playbook, for example, does it address, threat detection, incident response, threat mitigation, investigation, a combination of the aforementioned, etc.
- Playbook Activities & Playbook Processing: These properties enable organizations to better understand what a playbook does in detail and what features it has implemented such as conditional logic, digital signatures, etc.
- Versioning:Versioning enables organizations to track changes in their playbooks over time and potentially changes in playbooks created by different authors.
- Labels: Labels can be used to index and categorize playbooks by type, organization, and function while enabling many other organizational and trust group specific vocabularies or taxonomies. Labeling can be extremely powerful and effective when organizing playbooks.
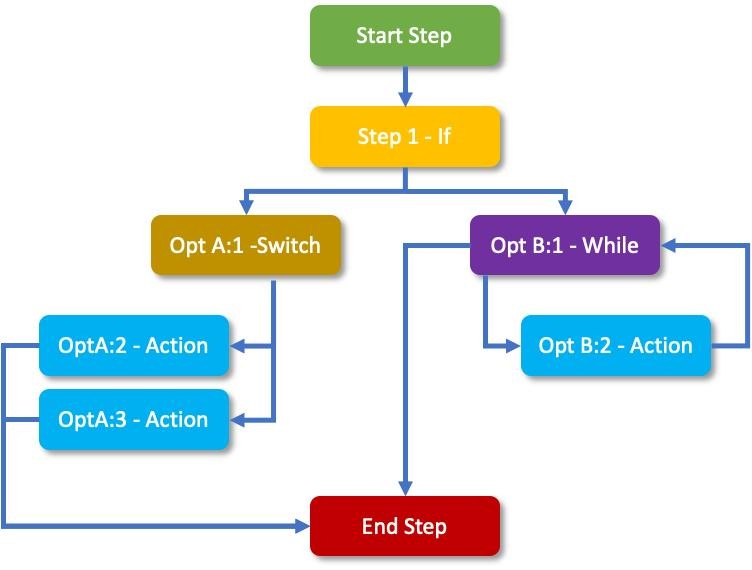
Figure 6: CACAO Workflow Steps.
Workflow Steps are the primary content that defines the playbook and the outcomes expected by executing the steps within it. CACAO provides a rich set of (programming) constructs, offering organizations a great amount of flexibility and comprehensive support for their operational and automation needs.
Steps may include:
- Sequential: Each step is executed in a simple defined order: step 1, step 2, step 3, step n
- Parallel: Each step is executed in parallel: step 1.1, step 1.2, step 1.3, step 1.n
- Conditional: Each step can consider a boolean expression prior to executing the next step, for example, if Condition X is true, then perform step 1.
- Loops: Supports repeating steps until a condition is not satisfied, for example, while Condition X is true, then perform step 1.
- Action: Supports the specific action to be executed for a given step.
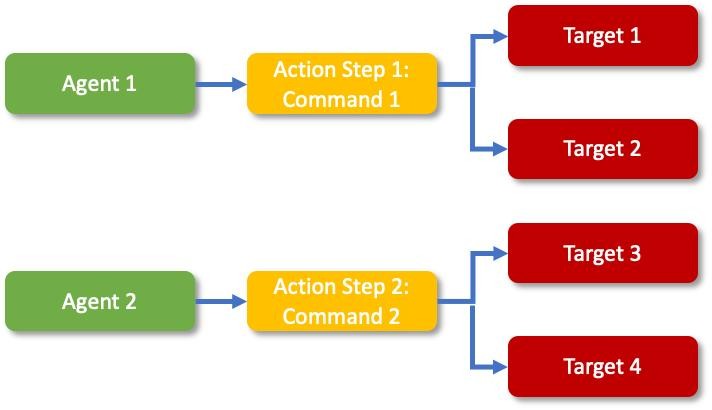
Figure 7: CACAO Agents & Targets.
Two simple examples:
- An agent could be an orchestration system executing an automated command (e.g., HTTP API call) to configure a firewall (in this case - the target).
- A human agent executing a manual step (manual command), such as switching off the power to a building's internet connection, which requires network isolation and is impossible to automate without a human override.
Conclusion
CACAO provides organizations with a rich set of mechanisms to define security playbooks across their entire organization to handle many different aspects of the security operations lifecycle. For collaborating teams within the organizations or across different organizations, CACAO enables the teams to define and share their defensive tradecraft on many aspects including incidents, threat responses, investigative actions, and security assessments.
Please check out the CACAO specification here and check back in the coming months for our webinar series on CACAO.
