Towards Incident Response Orchestration and Automation for the Advanced Metering Infrastructure
Author: UiO 
The Advanced Metering Infrastructure (AMI) represents a vital component of modern energy systems, facilitating the real-time collection and exchange of electricity consumption data through smart meters. These smart meters play a crucial role in maintaining grid stability, forecasting energy demand, and ensuring efficient energy distribution. However, the increasing frequency and sophistication of cyber-attacks pose significant threats to the reliability and security of AMI systems. This blog post explores the necessity of automating incident response in AMI environments, detailing a method based on the OASIS Collaborative Automated Course of Action Operations (CACAO) standard.
Note: This blog post is based on the paper: A. Lekidis, V. Mavroeidis, and K. Fysarakis, "Towards Incident Response Orchestration and Automation for the Advanced Metering Infrastructure," 2024 IEEE 20th International Conference on Factory Communication Systems (WFCS), Toulouse, France, 2024, pp. 1-8, doi:10.1109/WFCS60972.2024.10540775.
Background and Challenges: The Structure and Importance of AMI
AMI includes smart meters, communication networks, and data management systems. Smart meters, deployed in residential, commercial, and industrial settings, transmit consumption data to the AMI Headend, a central platform that collects, validates, and processes this data. This setup is crucial for tasks like load forecasting, outage management, and automated billing.
The communication between smart meters and the AMI Headend typically uses protocols like DLMS/COSEM over cellular networks (e.g., GPRS, 3G). This communication infrastructure ensures the accuracy and timeliness of electricity consumption data, which is essential for maintaining grid stability and optimizing energy distribution
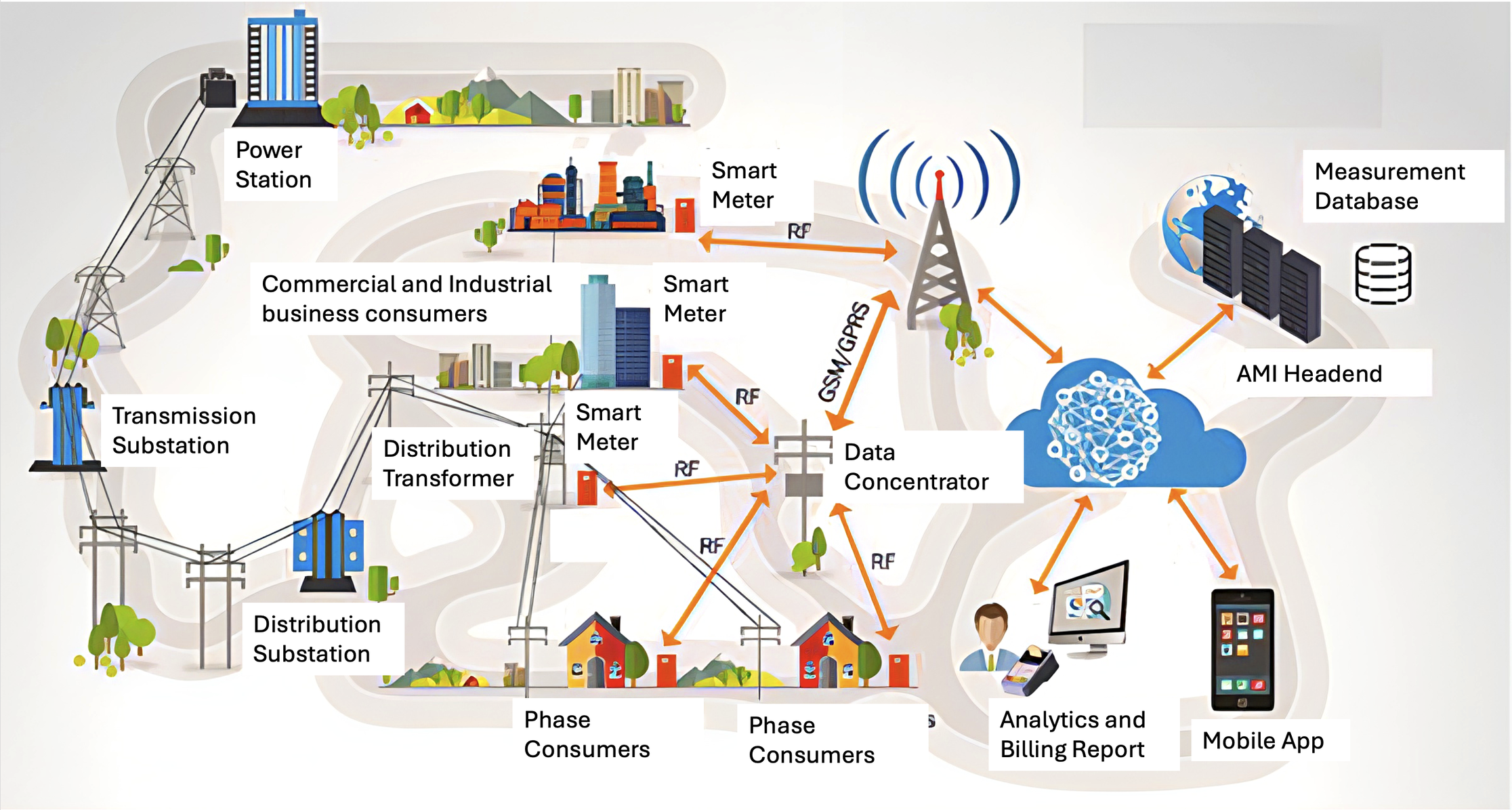
Figure 1: Advanced Metering Infrastructure Communication. This figure depicts the components and communication flow within the AMI ecosystem, highlighting the role of smart meters and the AMI Headend in data collection and processing.
Current Incident Response Methods and Their Limitations
Despite the importance of AMI, many utilities still rely on manual incident response methods. Studies indicate that 35% of utilities lack a formal incident response plan, and those that do often depend on manual actions by operators and IT personnel. This manual approach is time-consuming and prone to errors, leading to delays in threat detection and response. For example, when smart meter data cannot be transmitted due to network or cybersecurity issues, utilities often revert to traditional metering methods, which are inefficient and labor-intensive.
The unavailability of smart meter data can have cascading effects, impacting critical utility services such as energy demand forecasting. This can result in load demand peaks and potential blackouts, further highlighting the need for a robust incident response strategy.
The Need for Automation: The Case for Automated Incident Response
The complexity and scale of modern AMI systems necessitate an automated approach to incident response. Automation can significantly enhance the speed and accuracy of threat detection and response, reducing the reliance on manual processes and minimizing the risk of human error. Automated incident response ensures continuous service availability, even in the face of sophisticated cyber-attacks, and helps utilities comply with stringent regulatory requirements such as the NIS2 Directive.
Automated incident response systems can integrate with existing cybersecurity tools, providing a cohesive and comprehensive defense mechanism. By leveraging technologies like Security Orchestration, Automation, and Response (SOAR) and Extended Detection and Response (XDR), utilities can achieve a higher level of cyber resilience.
Incident Response Playbooks and Automation: What Are Incident Response Playbooks?
Incident response playbooks are formal documents outlining the processes and actions to be taken in response to specific types of cyber incidents. These playbooks provide a structured approach to threat detection, containment, eradication, and recovery, ensuring that all necessary steps are followed promptly and efficiently.
The CACAO Standard
The OASIS Collaborative Automated Course of Action Operations (CACAO) standard provides a common schema for developing interoperable, automatable, and shareable incident response playbooks. This standard enables organizations to create detailed, machine-readable playbooks that can be executed automatically, enhancing the speed and effectiveness of their incident response efforts.
CACAO playbooks can be integrated with various cybersecurity tools, allowing for seamless orchestration and automation of incident response activities. This integration supports the execution of predefined actions, such as isolating infected systems, deploying patches, and generating incident reports.
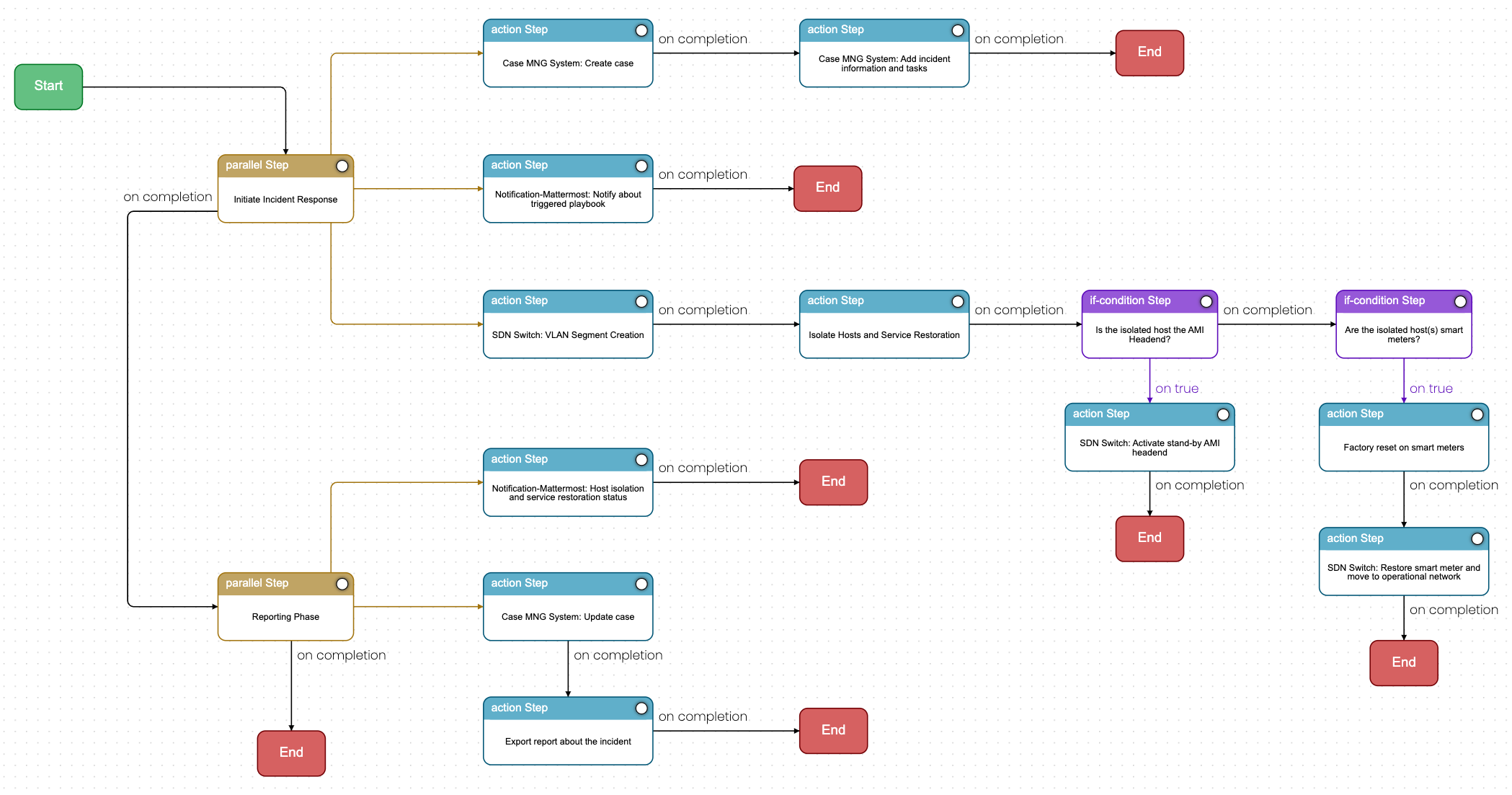
Figure 2: CACAO Playbook Executed by the ROAR Component. This figure visually represents an example of a CACAO playbook, illustrating how automated responses are structured and executed.
Implementing Automated Incident Response in AMI:
Preparation
The first step in implementing an automated incident response plan is preparation. This involves defining the incident response team, establishing communication channels, deploying necessary security controls, and conducting regular training sessions. Utilities should perform periodic risk assessments to identify potential threats and vulnerabilities within the AMI system, ensuring that they are adequately prepared to handle any incidents that may arise.
Detection and Analysis
Continuous monitoring of smart meter data and network activity is crucial for early detection of anomalies and potential cyber threats. Network Detection and Response (NDR) tools, integrated with Security Information and Event Management (SIEM) systems, provide real-time alerts and forensic capabilities to investigate the root causes of incidents. These tools help utilities quickly identify and analyze suspicious activities, enabling a rapid and informed response.
Containment
Once an incident is identified as a cyber-attack, containment procedures are initiated to isolate infected systems and prevent further propagation. This may involve reconfiguring network segments, updating firewall rules, and deploying hot standby devices to maintain service continuity. Automated containment actions can be executed through predefined playbooks, ensuring a swift and coordinated response.

Figure 3:Infected Host Isolation in a VLAN Through SDN Switch. This figure demonstrates how infected hosts were isolated in the network, providing a visual representation of the containment process.
Eradication and Recovery
Eradication involves removing the threat from the system, which may include reinstalling firmware, resetting configurations, and applying necessary patches. Recovery ensures that the system is restored to full operational capacity, often involving the activation of backup devices to maintain continuous service during the remediation process. Automated playbooks can streamline these steps, reducing downtime and ensuring a thorough and efficient recovery.
Incident Reporting
Comprehensive incident reporting is essential for compliance with regulatory requirements. Automated tools can facilitate the generation and dissemination of detailed incident reports, ensuring timely communication with relevant authorities. This includes submitting initial warnings, detailed notifications, and final reports, as mandated by regulations such as the NIS2 Directive.
Case Study: AMI Testbed
Testbed Setup and Emulated Attacks
To validate the proposed method, a realistic AMI testbed was established, including smart meters and an AMI Headend. The testbed was divided into different network segments to isolate critical systems and simulate real-world conditions. Two common cyber-attack scenarios were emulated: False Data Injection (FDI) and Distributed Denial of Service (DDoS) attacks.
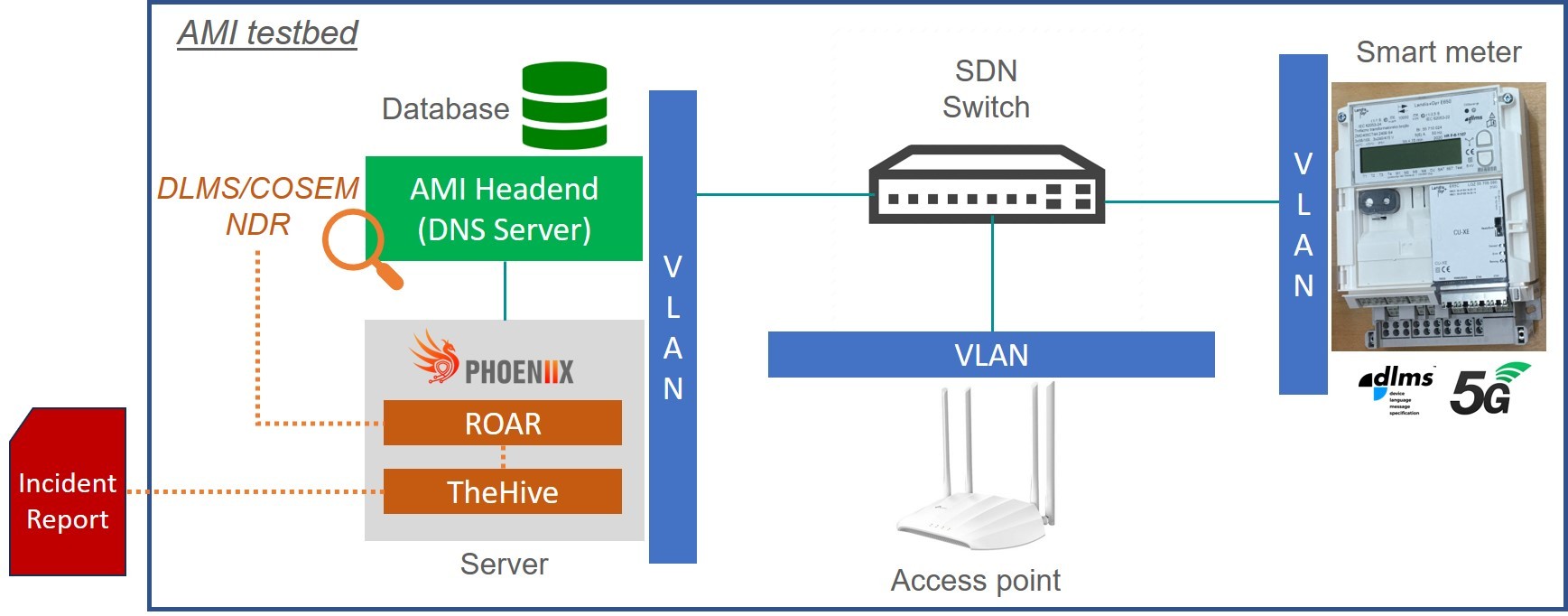
Figure 4:AMI Testbed Architecture. This figure provides a clear understanding of the testbed environment used for validation.
Automated Response Execution
Detection tools identified the attacks, triggering the execution of CACAO playbooks to automate containment and remediation actions. For instance, during an FDI attack, the system isolated compromised smart meters and reinstalled clean firmware. During a DDoS attack, load balancing and firewall updates mitigated the threat, ensuring continuous service availability.
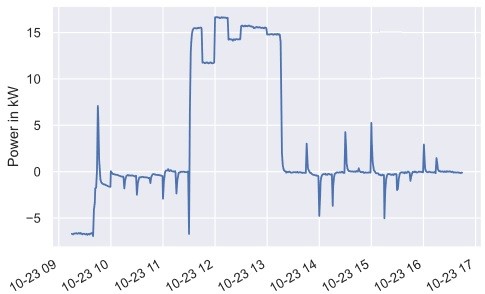
Figure 5:Emulated FDI Attack in the Apparent Power. This figure illustrates the impact of the FDI attack on power measurements, showing the data anomalies caused by the attack.
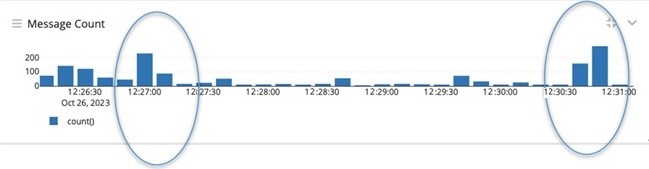
Figure 6:Smart Meter DLMS/COSEM Messages During the DDoS Attack. This figure shows the increase in network messages during the DDoS attack, highlighting the detection and response process.
The automated response significantly reduced the Mean Time To Respond (MTTR) by 96% for FDI attacks and 98% for DDoS attacks, demonstrating the effectiveness of the proposed approach in enhancing the resilience of AMI systems.
Future Directions
Advancements and Ongoing Research
Future research will focus on simulating large-scale cyber-attacks, including malware spreading and cascading impacts on business continuity. Additionally, the integration of smart meters with emerging technologies such as Electric Vehicle (EV) charging will be explored, ensuring comprehensive security across all aspects of the energy sector. Continuous improvement and adaptation of automated incident response strategies will be essential to address evolving threats and maintain the integrity of AMI systems.
Conclusion
The orchestration and automation of incident response in AMI systems, facilitated by CACAO playbooks, represent a significant advancement in ensuring the security and reliability of critical infrastructure. By reducing response times and improving the accuracy of incident handling, utilities can maintain continuous service availability, comply with regulatory requirements, and enhance overall cyber resilience. The approach presented in this blog post provides a blueprint for utilities to adopt and implement these practices, safeguarding the critical infrastructure that underpins our daily lives. As the energy sector continues to evolve, automated solutions will be indispensable in mitigating cyber threats and ensuring the stability of our power grids.
