Utilizing an Enhanced STIX 2.1 Representation of MITRE ATT&CK as Cyber Threat Intelligence Source for Adversary Filtering
Author: UiO The exponential increase in cyberattacks and sophisticated attack behavior push organizations to continuously invest in strengthening their cybersecurity posture (Brown & Lee 2021)1. Defenders to better respond to the current cyber threat landscape, improve their threat situational awareness, and stay resilient against cybersecurity threats have recognized the need to generate and utilize cyber threat intelligence and collaborate through information exchange to use others' experiences and knowledge as their own organization's defense (Johnson et al. 2016)2.
One highly used and well-maintained cyber threat intelligence source is MITRE ATT&CK. ATT&CK (Adversarial Tactics, Techniques, and Common Knowledge) is a globally-accessible knowledge base concerning adversary behavior. The effort is led by MITRE and supported by the broader cybersecurity community via contributions. ATT&CK focuses on how adversaries compromise and operate within computer information networks. Further, under the same framework, MITRE maintains a knowledge base of adversaries3 (referred to as Groups) and their technique use. Groups are sets of related intrusion activity that are tracked by a common name in the security community and are aimed to collect ATT&CK techniques and software that have been reported to use. Concretely, the ATT&CK framework is a collection of tactics and techniques used by adversaries, organized into a matrix that allows organizations to identify the specific threats they face and take appropriate action to defend against them.
When defenders detect and respond at the Tactics, Techniques, and Procedures (TTPs) level, they operate directly on adversary behavior. Such detection can identify malicious activity that may not rely on prior knowledge of adversary tools and atomic indicators and can have a lasting impact on the attackers as they would have to change nearly every aspect of how they operate to avoid detection (Lee & Brown 2021)4. Being able to track and detect adversaries at the TTP level is challenging. However, when successful, the adversaries will be forced to change their modus operandi to remain undetected, which is a costly process. David Bianco depicts that through the “pyramid of pain” (Bianco 2014)5. Bianco's pyramid of pain is shown in Figure 1 and represents the pain an adversary will suffer when a defender can deny the use of those indicators. At the apex of the pyramid of pain are Tactics, Techniques, and Procedures (TTPs) as a single grouping.
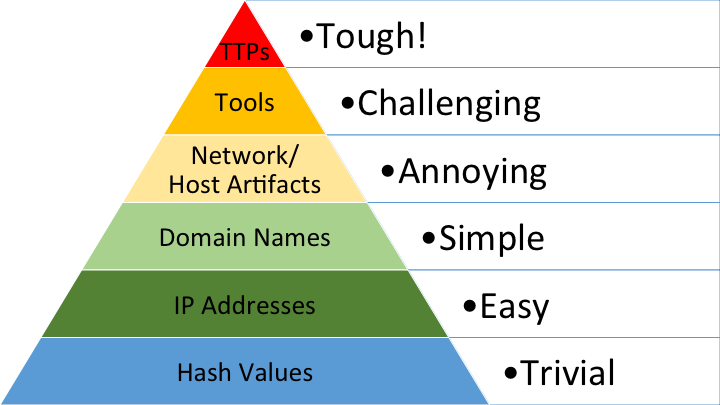
Figure 1: The Pyramid of Pain (Bianco 2014)5.
Being able to filter intrusion sets of interest is a valuable but also time-consuming activity. In the context of ATT&CK Groups many properties that can support filtering appear in textual descriptions introducing a degree of difficulty in performing tailored queries. In this research, we have enhanced the existing representation approach (model) of ATT&CK Groups v9 in STIX 2.1 by extracting the available textual but contextual information and making it available in a fully structured manner. Consequently, we can significantly speed up the filtering process to find the relevant adversaries. The Groups knowledge base describing known adversaries consists of fields like name, id, descriptions, techniques used, software used, etc. Of particular importance is the Group's “description” property that, in many cases, carries information about a adversaries' motivation, the country it originates from, as well as sectors and countries that have been targeted. This unutilized hidden information was what triggered our research activity, as this information is a valuable asset when made queryable.
MITRE's STIX 2.1 Representation of ATT&CK Groups
The STIX standard developed by the OASIS Cyber Threat Intelligence Technical Committee is a common language and serialization format used to represent and exchange cyber threat intelligence (Jordan, Piazza & Darley 2021)6. For programmatic utilization, MITRE provides access to the ATT&CK knowledge base through STIX interfaces on their GitHub7.
Figure 2 illustrates the set of STIX 2.1 object and relationship types leveraged to define and describe groups that altogether comprise the ATT&CK Groups knowledge base. An “intrusion set” object (activity group or Group) connects with “attack pattern” objects (techniques/sub-techniques), “malware” objects (software), and “tool” objects (software).
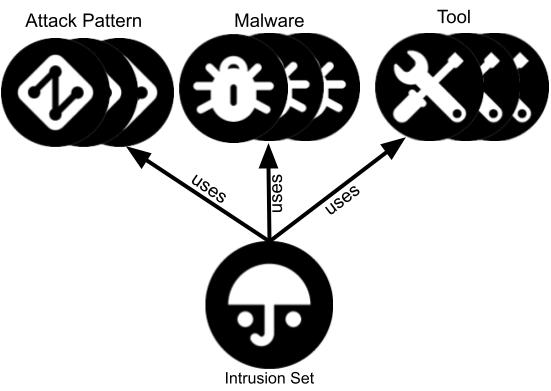
Figure 2: High-level STIX 2.1 representation of the Groups knowledge base.
A Proposed Enhanced STIX 2.1 Representation for the ATT&CK Groups Knowledge Base
Our enhanced model introduced additional types of contextual information that rely on information already part of the knowledge base but represented in a semi-structured form. This enhancement enabled us to construct more intelligible queries and exploit the knowledge base in a more granular manner. In particular, information from the descriptions of activity groups, which in many cases, identify group motivations, the countries they originate from, as well as sectors and countries they have targeted.
We have extracted the identified information and represented it in a fully structured manner using a set of distinct STIX 2.1 objects. In particular, the “location” object type is utilized to represent the suspected or confirmed country of origin of an activity group as well as targeted countries and regions. The “identity” object type is used to represent targeted sectors. Moreover, when feasible, the STIX 2.1 “intrusion set” objects are enriched with primary and secondary motivations (using the available primary and secondary motivations properties of the intrusion set object type). Figure 3 depicts the enhanced STIX 2.1 representation of the Groups knowledge base.
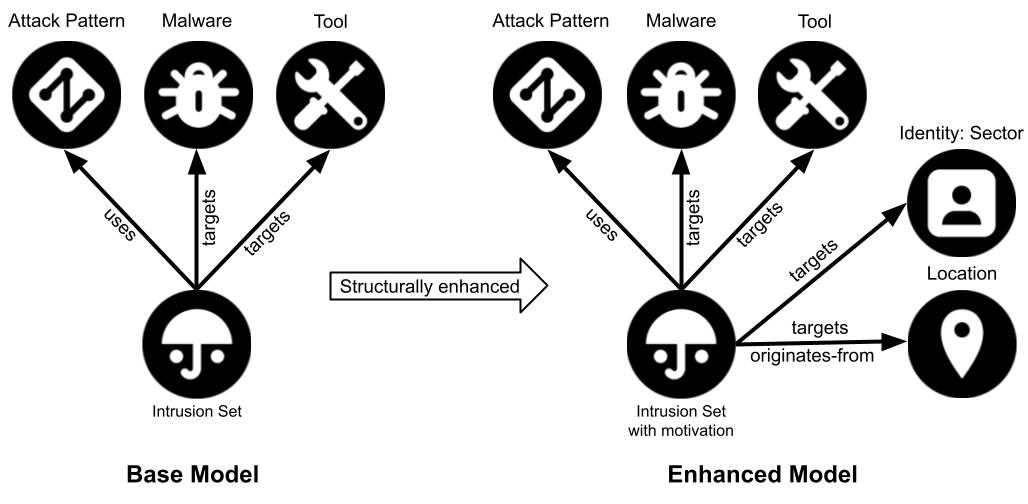
Figure 3: Enhanced STIX 2.1 representation of the ATT&CK Groups knowledge base.
MITRE ATT&CK v12 Campaigns
A release of MITRE ATT&CK v12 in October 2022 8, introduced the campaign concept to the MITRE ATT&CK framework. These campaigns describe any grouping of intrusion activity conducted over a specific period of time with common targets and objectives. A key aspect of Campaigns is that the activity may or may not be linked to a specific threat actor9. The vision for Campaigns is to provide users with another way to view the evolution of malicious cyber operations.
Similarly to groups, the campaigns include ID, name, and activity description. In addition, campaigns include details like known targeted countries and sectors but within the textual description field. A valuable improvement is the addition of temporality through the “First Seen” and “Last Seen” fields, which will help with identifying the time-relevant intrusions. The relationships of a campaign are related to the usage of techniques and software and attribution to a Group, as presented in Figure 4.
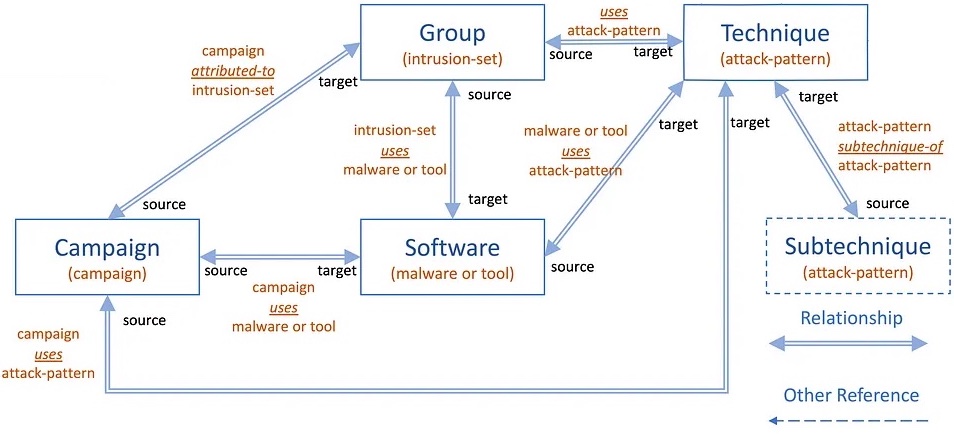
Figure 4: Relationships of the Campaign object.
In practice, the ATT&CK campaign object is represented using the STIX 2.0 Campaign object with two additional properties, “x_mitre_first_seen_citation” and “x_mitre_last_seen_citation.”
To programmatically gather and view all techniques utilized by a Group, the techniques need to be collected from all campaigns attributed to the Group, as the campaigns consist of a separate set of techniques. The same goes for showing a holistic overview of software usage, which will now include unattributed campaigns.
A Small Comparison to our SolutionATT&CK v12 brought a valuable improvement by introducing the Campaign object. It will help defenders with the temporality problem of adversaries. This information will tell the defenders if the campaign is known to be still ongoing and also how the adversaries change their capabilities and TTPs over time. There are still a few challenges to ATT&CK v12. Opposite to our solution, the origin and targeted countries, targeted sectors, and motivations remain hidden in textual description fields, although STIX 2.0/2.1 supports the structured representation of such information.
Utilizing the Enhanced STIX 2.1 Groups Knowledge Base for Group Filtering and Technique Prioritization
This section demonstrates the use of the new types of contextual information introduced in the enhanced STIX 2.1 representation of the Groups' knowledge base to filter activity groups of interest.
It is important to remark that the accuracy of the results retrieved might be questionable due to the use of non-standardized vocabularies in providing context that often leads to semantic ambiguity. For example, the number of sectors and types considered critical infrastructure might be dissimilar in different countries.
Listing 1 presents an SQL-based query that aims to retrieve activity clusters that are believed to originate from the Russian Federation and have targeted establishments within the Government sector in the United States. The results indicate three activity groups to be of relevance.
SELECT * FROM GroupsKnowledgeBase
|
Listing 1: SQL query leveraging our model's contextual information types to retrieve activity groups of interest.
We have retrieved the ATT&CK technique used of the groups and provided it as input to MITRE's ATT&CK Navigator to identify and explore any commonalities. The technique overlap is presented in Figure 5. The light red color techniques do not overlap among the three groups. The red color techniques indicate use by two groups, and the dark red color techniques indicate use by all three groups. Thus, indicating the importance and priority of handling these techniques.
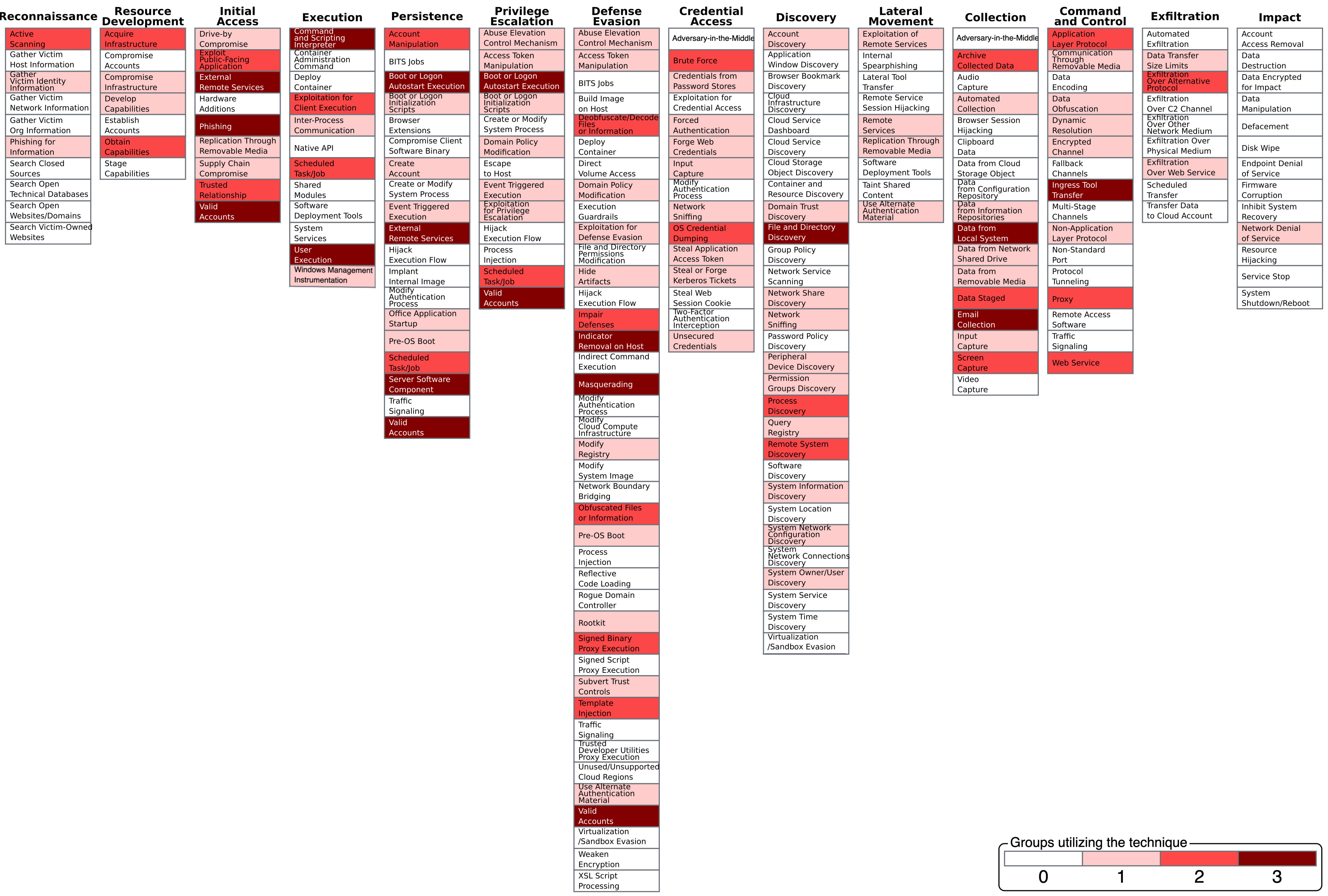
Figure 5: Heatmap showing commonalities in technique use among APT28, APT29, and Dragonfly 2.0.
You can read the full paper in the following url:
https://papers.academic-conferences.org/index.php/eccws/article/view/349/381
For technical details please visit our GitHub repo for this project:
https://github.com/fovea-research/SAG
- Brown, R. and Lee, R.M., (2021). 2021 SANS Cyber Threat Intelligence (CTI) Survey. In Tech. Rep. SANS Institute.
- Johnson, C., Badger, L., Waltermire, D., Snyder, J. and Skorupka, C., (2016). Guide to Cyber Threat Information Sharing. NIST special publi cation, 800(150).
- https://attack.mitre.org/groups/
- Lee, R.M., and Brown, R., (2021). FOR578 Cyber Threat Intelligence: 578.1 Cyber Threat Intelligence and Requirements. SANS.
- Bianco, D., (2019). The Pyramid of Pain (2014). Available at: http://detect-respond.blogspot.nl/2013/03/the-pyramid-of-pain.html.
- Jordan, B., Piazza, R., and Darley T., (2021), July, STIX™ Standard, version2.1 ed., [Online] https://docs.oasis-open.org/cti/stix/v2.1/stix-v2.1.html, OASIS Cyber Threat Intelligence Technical Committee.
- MITRE ATT&CK v12 Release Note MITRE ATT&CK v12 Release Note https://attack.mitre.org/resources/updates/updates-october-2022/
- Introducing Campaigns to MITRE ATT&CK https://medium.com/mitre-attack/introducing-attack-campaigns-6b15baa6cbb4
- STIX 2.0 Campaign: http://docs.oasis-open.org/cti/stix/v2.0/csprd01/part2-stix-objects/stix-v2.0-csprd01-part2-stix-objects.html#_Toc476230925
