Cyber Threat Intelligence - A necessity, not a luxury
Author: NCSA Cyber threat intelligence (CTI) refers to collecting, analyzing, and disseminating information about emerging or current cyber threats. It involves gathering and analyzing data from various sources to identify potential threats and vulnerabilities and then using that information to develop strategies for preventing, detecting, and responding to cyber-attacks. CTI has emerged as a vital field of interest in response to the constantly changing and intricate threat environment, and there is growing enthusiasm among both academia and organizations to understand its applications, benefits, data sources, and the transformation of data into actionable intelligence. However, it is still not a clearly defined field compared with other threat Intelligence fields, like defense, law enforcement, and public health.
One of the most common approaches to CTI categorization divides CTI into strategic, operational, and tactical categories. Strategic CTI is focused on long-term planning and decision-making, while operational CTI is focused on day-to-day operations, and tactical CTI is focused on specific incidents or events. Other approaches include further categories, like technical CTI, which is generally short to medium-term, with a focus on identifying technical vulnerabilities and threats, or human CTI, which is typically short to medium-term, with a focus on understanding the motivations and intentions of threat actors. Overall, the expectations regarding time perspective and analysis scope for each category of CTI may vary depending on the organization's needs and goals, but these general guidelines can be useful for understanding the different types of CTI and their respective focuses. In the following figure, four CTI types are presented in relation to information assortment, knowledge analysis, and intelligence consumption [1].
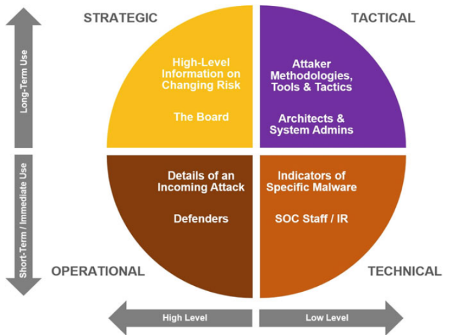
Figure 1: CACAO Architecture.
Regardless of the CTI category, the selection of CTI feeds is crucial for CTI's added value. CTI feeds are sources of information about current and emerging cyber threats and attacks, and they can be obtained from various providers such as government agencies, commercial vendors, and open-source communities. Organizations could use both internal and external CTI sources. Internal Sources include raw technical data (logs, traffic. etc.) or processed threat information and alerts from advanced security solutions (SIEM, EDR, NDR). External Sources cover a wider range of information, and they could be indicatively categorized as:
- Open-source intelligence (OSINT) feeds, cost-free, with considerations regarding their quality, collection effort, and analysis methods. Private sector or Cybersecurity Institutes and Agencies free seeds could be considered OSINT, but the main sources of information are the web (surface, Deep and Dark) and social media.
- Private or commercial sources: These are usually paid; however, in some cases, there is a free version where not all features are available.
- Cybersecurity Institutes and Agencies, like The National Institute of Standards and Technology (NIST) of the US Department of Commerce or the US Cybersecurity and Infrastructure Security Agency (CISA).
- Shared feeds between trusted organizations with similar scope and objectives, like the European Cyber Security Incident Response Teams (CSIRTs) and the Cyber Crises Liaison Organization Network (CyCLONe).
To maximize the value of CTI, it is important to carefully select the information sources relevant to the organization's industry, assets, and threat landscape. In other words, the quality and relevance of CTI feeds directly impact the effectiveness of an organization's CTI program. Moreover, selecting the right CTI feeds can also help in reducing the amount of noise and false positives that security teams must deal with, making it easier for them to focus on the most critical threats and prioritize their responses accordingly. Several free and open-source CTI feeds are available, and even if they may not usually provide the same level of quality and coverage as paid CTI feeds, a careful evaluation and selection of free CTI feeds can provide valuable information.
Data formats play a crucial role in facilitating the sharing and compatibility of Cyber Threat Intelligence (CTI). Open formats - such as JSON, XML, and CSV - hold significant value in promoting interoperability. In the realm of cybersecurity, diverse data formats are employed for representing threat intelligence and enabling information sharing. Notably, these formats encompass enumerations, scoring systems, and sharing standards, as identified in [2]:
| Common data formats for threat intelligence representation and information sharing | ||
| Enumerations | Scoring Systems | Sharing Standards |
|
|
|
Table 1: Common CTI Data Formats.
As part of the JCOP project, we evaluated free CTI feeds based on their community activity and update frequency and their compatibility with the OpenCTI platform [3], which is used as the main CTI platform of JCOP.
Some examples of useful free CTI feeds are:
- The National Vulnerability Database (NVD) [4]: This free vulnerability database provided by the National Institute of Standards and Technology (NIST) contains information about known vulnerabilities in software and hardware products.
- The Common Vulnerabilities and Exposures (CVE) database [5]: This is a free public database of common vulnerabilities and exposures maintained by MITRE. CVE identifiers are used widely to track and identify vulnerabilities in software and hardware.
- MITRE Datasets [6]: This is a free CTI feed used for organizing CTI sources, like tactics, techniques, and procedures (TTPs), advanced persistent threats (APTs), malware, intrusion sets, attack patterns, etc.
- AbuseIPDB [7]: This is a free database of IP addresses that have been reported for malicious activity, including spam, hacking, and malware distribution. The database can be used to identify potentially malicious IP addresses and block them from accessing an organization's network.
- Cybercrime Tracker RSS feeds [8]: A site containing information about botnets, malicious IP addresses, and C&C servers.
- CISA Known Exploited Vulnerability (KEV) catalog [9]: A list of registered CVEs for which there is reliable evidence that the vulnerability has been actively exploited in the wild or there is a clear remediation action for the vulnerability, such as a vendor-provided update.
In conclusion, the utilization of Cyber Threat Intelligence (CTI) is not just a luxury but a necessity for organizations, and particularly for National Cybersecurity Authorities, due to their responsibility of protecting critical infrastructure entities, government systems, and national security interests. CTI enables these authorities to gather intelligence about potential cyber threats targeting the country's assets, critical sectors, or government agencies. It helps enhance situational awareness, facilitating early-warning systems and supporting incident response at a national level. CTI also assists in fostering collaboration and information sharing among various organizations, both within and across national boundaries, to combat cyber threats collectively.
Resources- Montasari, R., Carroll, F., Macdonald, S., Jahankhani, H., Hosseinian-Far, A., & Daneshkhah, A. (2021). Application of Artificial Intelligence and Machine Learning in Producing Actionable Cyber Threat Intelligence. Advanced Sciences and Technologies for Security Applications, 47-64. https://doi.org/10.1007/978-3-030-60425-7_3
- Mavroeidis, V., & Bromander, S. (2017, September). Cyber threat intelligence model: an evaluation of taxonomies, sharing standards, and ontologies within cyber threat intelligence. In 2017 European Intelligence and Security Informatics Conference (EISIC) (pp. 91-98). IEEE.
- https://github.com/OpenCTI-Platform/opencti
- https://nvd.nist.gov/vuln/data-feeds
- https://cve.mitre.org/cve/data_feeds.html
- https://attack.mitre.org/resources/working-with-attack/
- https://www.abuseipdb.com/
- https://cybercrime-tracker.net/
- https://www.cisa.gov/known-exploited-vulnerabilities-catalog
